FIPS-Validated. Always Verified.
FIPS 140-3 validated cryptography, built into our hermetic build system, ensures secure containers from build to runtime.

.png)
Why FIPS 140-3 Matters
FIPS 140-3 defines the standard for trusted cryptography. It governs how encryption must be implemented and proven in regulated industries. 79% of organizations have delayed releases due to security or compliance gaps. FIPS exists to close that risk.

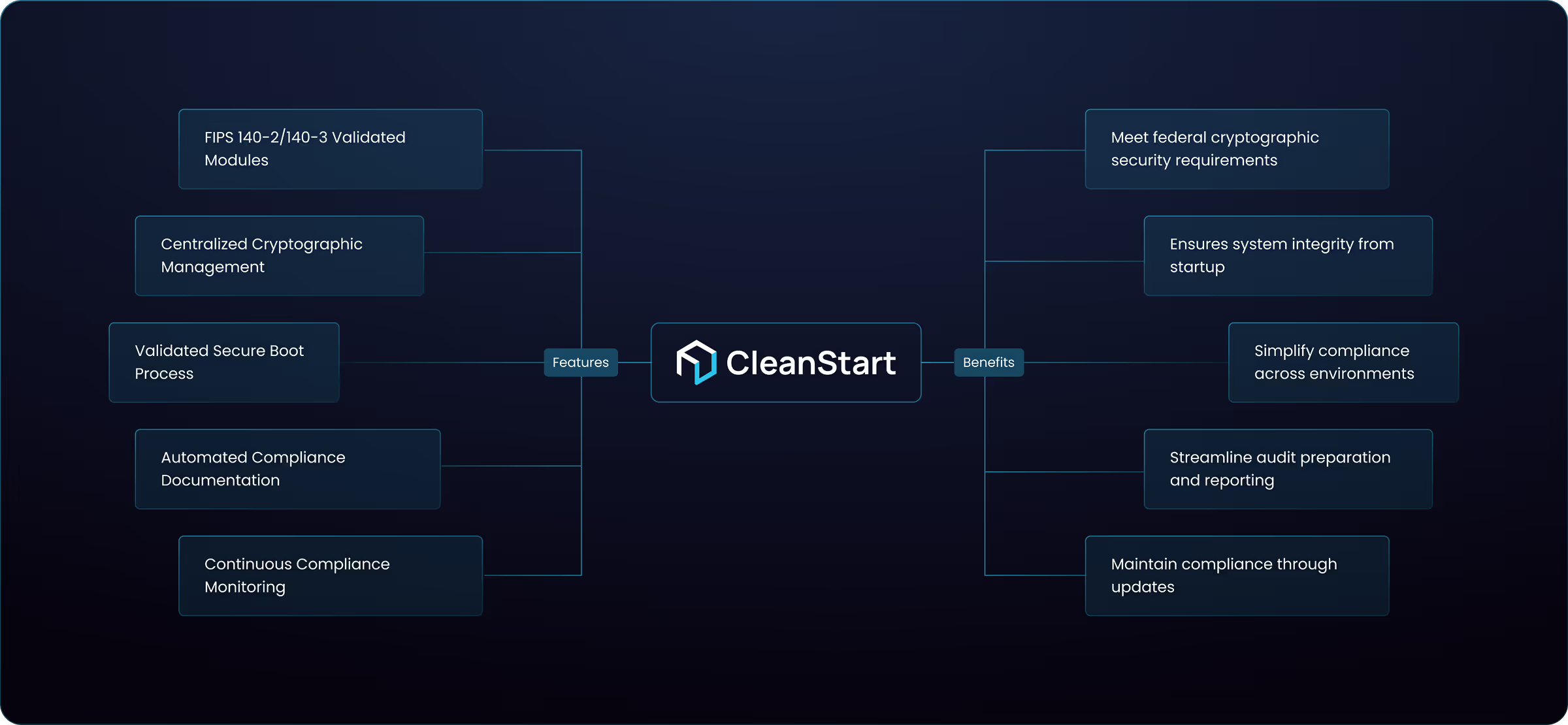
Validated Cryptographic Modules

Centralized Cryptographic Management
Secure Boot Process
Ensures encryption functions are correctly designed, tested, and verified for secure use.

Validated
Secure Boot Process

Automated Compliance Documentation

Continuous Compliance Monitoring
How CleanStart Enables FIPS 140-3 Compliance
CleanStart embeds this validation directly into every build, making compliance continuous, not manual.
CleanStart FIPS 140-3 Maturity Model
A four-stage framework that demonstrates how CleanStart moves from crypto design to ongoing compliance at scale.
.svg)
Defines the cryptographic boundary and deterministic build prerequisites.
.svg)
Enforces approved algorithms, modules, and key management by design.
.svg)
Proves cryptographic correctness through automated testing and evidence.
.svg)
Sustains control and validation across every build with drift detection
Use Cases
With FIPS validation built into every build, CleanStart accelerates compliance while enabling secure deployments across regulated environments.




The ROI of Built-In Compliance
CleanStart shifts FIPS compliance from a manual effort to an automated outcome, reducing audit timelines, operational overhead, and certification risk.

%
faster in Time-to-Compliance
%
reduction in Operational Costs
%
improvement in Development Productivity



.webp)
.webp)
.webp)







%20(1).png)





.svg)
.svg)
.svg)
.png)