

Bigger Images, Bigger Risk
Public Images Are Bloated
Inherited Vulnerabilities
Risk exists before application
code is added.
Too Many Components
Public images include packages
most workloads never use.
Oversized SBOMs
More components to track, justify, and audit.

Constant Patching
The same base issues reappear release after release.
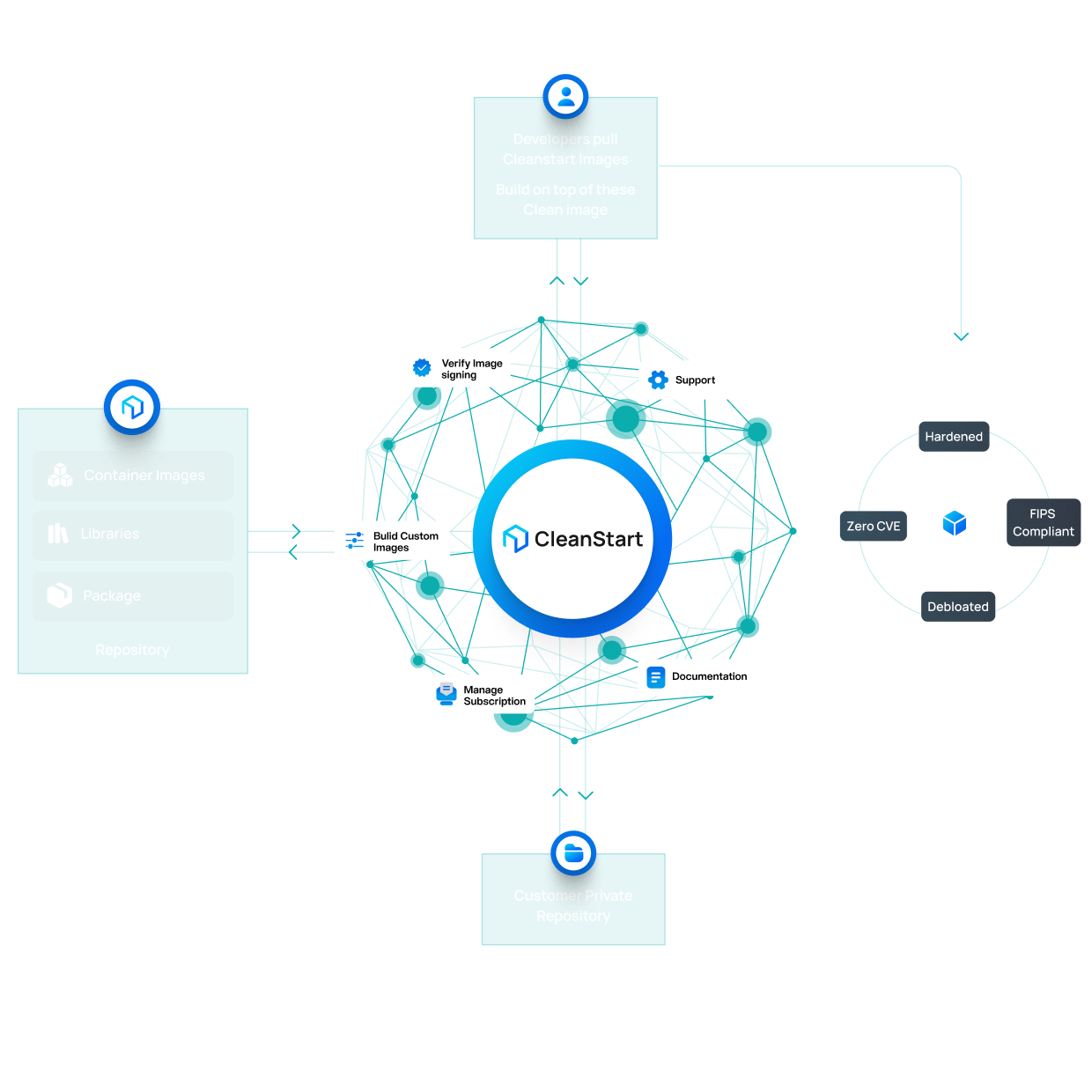
The CleanStart Approach
.png)
Minimal
Foundations
Only required components are included in every image
Unnecessary
Components
Shells, package managers, and unused tools are excluded.
.png)
Deterministic
Builds
Images are built consistently from trusted source.

Secure Defaults
Applied
Hardened configurations are enforced at the image layer.
What This Delivers
Reduced Vulnerability Exposure
Fewer exploitable components exist at image pull time.
.png)
Smaller CVE Backlog
Less recurring remediation across builds and releases

Focused SBOMs
Only meaningful components to track and defend
.png)
Lower Operational Load
Less scanning, patching, and rework for teams.
.png)
Built for Modern Production Environments

Kubernetes Platforms
Production clusters running containerized workloads.

Regulated Environments
Workloads with compliance and audit requirements.

Security-Focused Teams
Teams prioritizing prevention
over remediation.
Fits Into What You’ve Already Built

01
.png)
Drop-In Images
Replace public base images without changing workflows.
%20(1).png)
02
.png)
Pipeline Compatible
Works with existing CI/CD and registries.

03
.png)
Deploy Anywhere
Supports Kubernetes and container platforms.
.png)



.webp)
.webp)
.webp)







%20(1).png)





.svg)
.svg)
.svg)
.png)