
Prove What Your Software Is Built On
Security, compliance, and traceability you can defend in any audit or board review
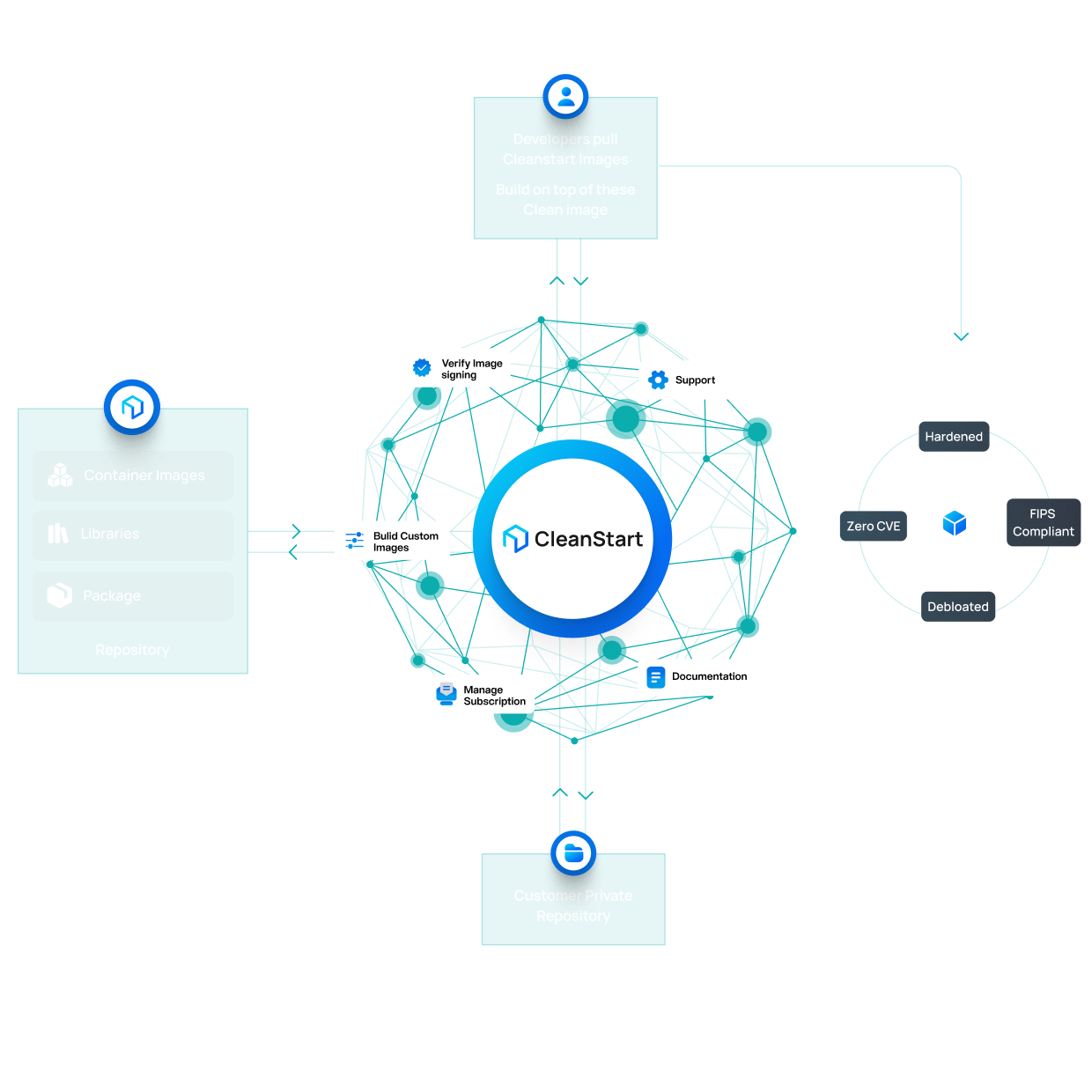
The Supply Chain Is Now Your Weakest Link
Traditional Security Limitations
Modern supply chain risk does not come from a single failure.
It accumulates across multiple blind spots that traditional security was never designed to govern.
Vulnerabilities discovered late in the software lifecycle cost orders of magnitude more to remediate than those addressed early. Supply chain attacks exploit this gap by reaching production before traditional controls ever engage.
Outcomes That Matter at Enterprise Scale
Directly aligned to CSO priorities: risk, compliance, and efficiency.
.svg)
Reduce Exposure Windows
Live rebuild and provenance mapping limit zero-day impact.
.svg)
Strengthen Software Build Integrity
Artifacts are built, signed, and verified with full lineage.
.svg)
Eliminate Supply-Chain Blind Spots
Gain visibility into build, install, and dependency risks.
.svg)
Prove Compliance on Demand
Generate instant, verifiable attestation packets.
.svg)
Accelerate Incident Response
Identify impacted components and rebuild within minutes.
.svg)
Cut Security Tool Sprawl
Unify scanners and policies into one assurance layer.
.png)
End-to-End Assurance from Source to Production
Continuous verification and enforcement across the entire software lifecycle.
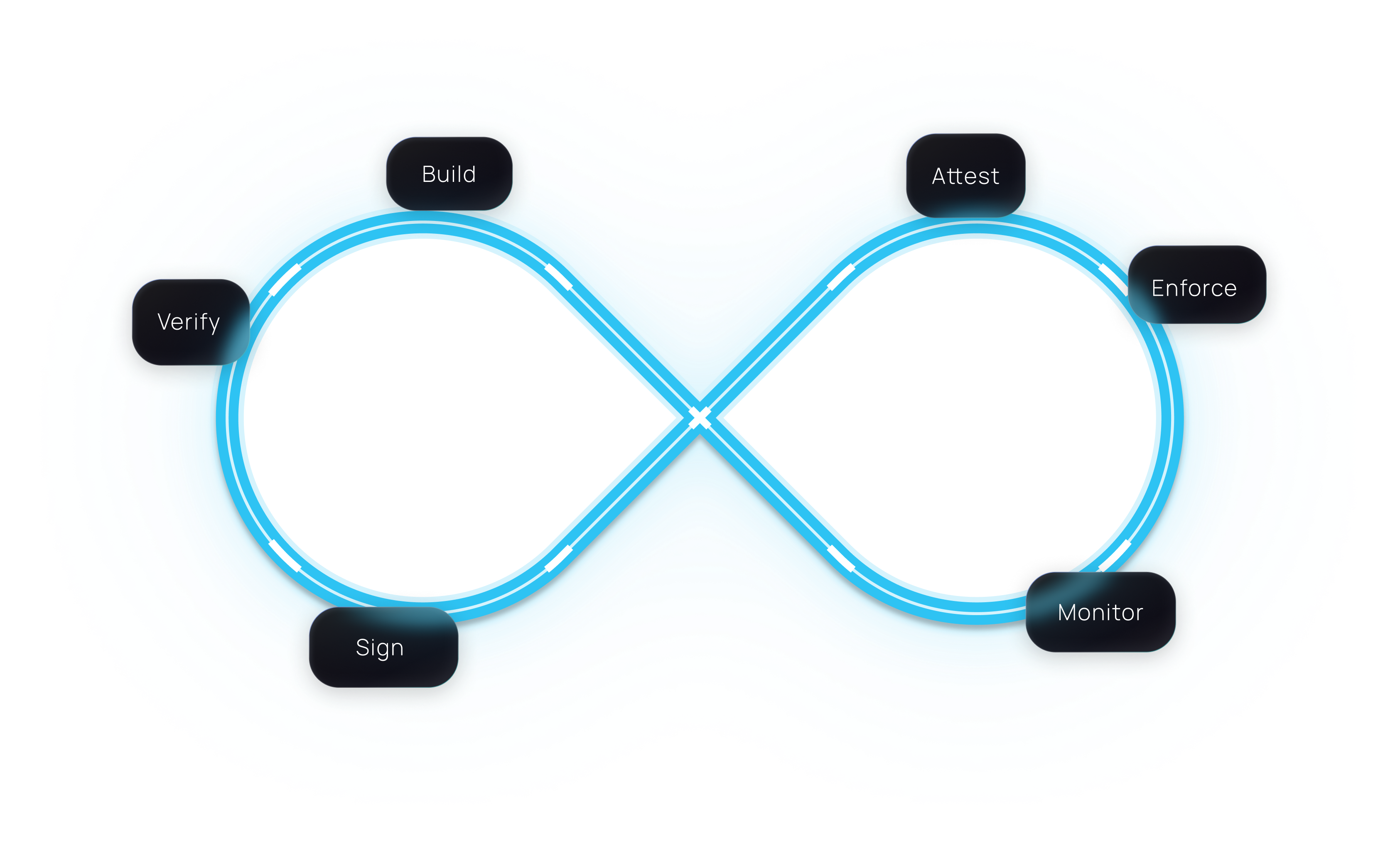
Every stage is verified , signed,and continuosly governed.
Tools for Your Next Audit, Risk Review, or Board Meeting
Built to support audits, risk reviews, and executive reporting.
Built for Regulated and High-Stakes Environments
.svg)
Proof for Auditors
Continuous, verifiable evidence for regulatory reviews.
.svg)
Zero-Day Containment
Rapid traceability and rebuilds during supply chain incidents
.svg)
Dependency Governance
Visibility into open-source and third-party components
.svg)
Policy Enforcement
Guardrails across every build and pipeline.
.svg)
Secure Release Readiness
Verifiable integrity before production deployment
.png)
Proof for Auditors
Continuous, verifiable evidence for regulatory reviews.
.png)
Zero-Day Containment
Rapid traceability and rebuilds during supply chain incidents
.png)
Dependency Governance
Visibility into open-source and third-party components
.png)
Policy Enforcement
Guardrails across every build and pipeline.
.png)
Secure Release Readiness
Verifiable integrity before production deployment
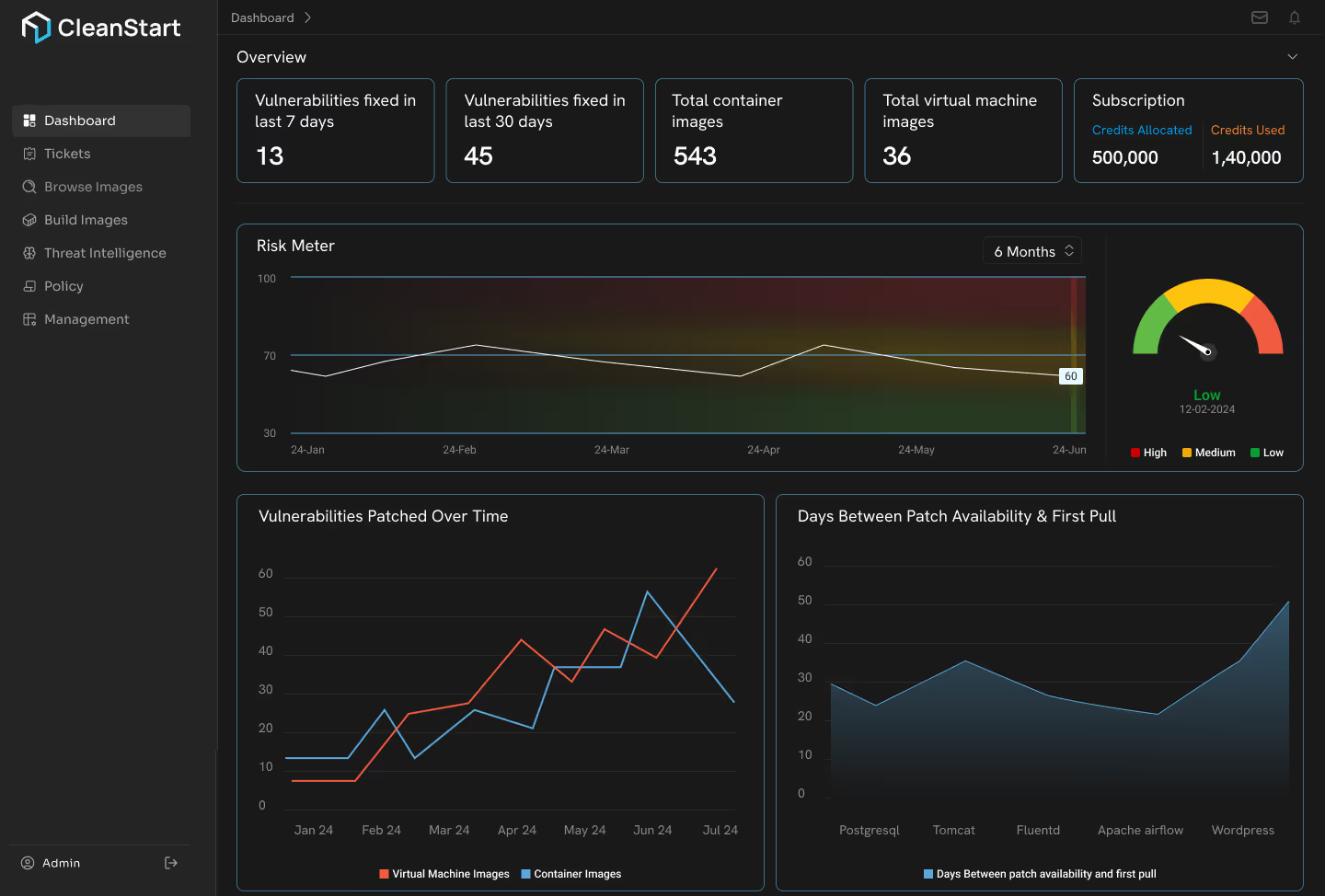
Security You Can Defend, Anywhere!
Your software isn’t judged by speed but by how provable it is.

.svg)
.svg)
.svg)
.svg)


.webp)
.webp)
.webp)







%20(1).png)





.svg)
.svg)
.svg)
.png)