
CVE fatigue occurs when container and platform teams are overwhelmed by vulnerability alerts, keep patching and rebuilding images, and still see their vulnerability backlog grow. With studies showing hundreds of CVEs per typical container image and 87% of production images containing critical or highseverity issues, it is clear that the current “fix everything” approach does not scale.
Introduction: CVE fatigue in container security teams
Modern Kubernetes and container platforms rely heavily on automated image scanning, which routinely flags long lists of critical and highseverity vulnerabilities. One widely cited cloudnative security report showed that 87% of container images in production have critical or highseverity vulnerabilities. Yet, only about 15% of those are in packages actually loaded at runtime, meaning most alerts do not represent real, exploitable risk for many workloads.
This gap between scanner noise and true runtime risk is the root of CVE fatigue: engineers stop trusting the reports, leadership becomes cynical about “red dashboards,” and security efforts turn into a game of compliance whackamole. The goal of this blog is to explain why container vulnerability backlogs keep growing, why updating base images is not enough, and how a reducedsurface, hardenedimage approach CleanStart's vulnerability remediation strategy helps you fix fewer CVEs by design while improving realworld security.
Why container vulnerability backlogs keep growing
Container backlogs grow for structural reasons, not because teams are lazy or careless. Several empirical studies have quantified how bad the problem is:
- A detailed analysis of container images found a mean of 460 vulnerabilities per image and a median of 321, with a strong correlation between package count and vulnerabilities.
- A supplychain risk study focusing on containers reported an average of 604 known vulnerabilities per container, with over 40 - 45% classified as critical or high severity, and many being years old.
When every container begins with hundreds of known issues, and new CVEs (Common Vulnerabilities and Exposures) are disclosed daily, your backlog naturally increases. Additionally, organizations often leave over 70% of vulnerabilities with available fixes unpatched in containers. This is because fully addressing all issues would significantly slow down release velocity and consume a substantial amount of engineering capacity. Resource
Inherited vs introduced vulnerabilities in container images
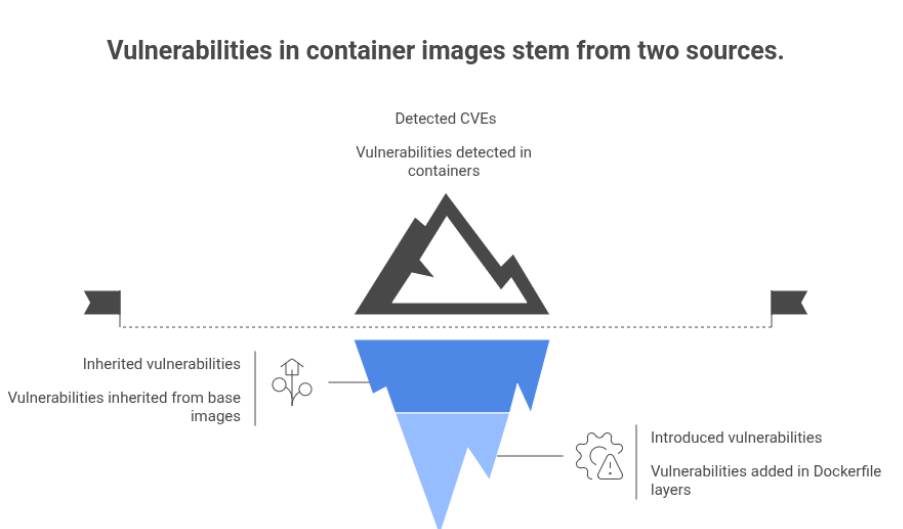
Understanding where vulnerabilities come from is key to breaking the cycle. In container images, there are two major categories:
- Inherited vulnerabilities
These are inherited from your base image and its parent layers, common OS images like Ubuntu, Debian, or community language runtimes. Studies show a large fraction of detected CVEs in application containers originates from these OS and base layers, because they include many utilities and libraries that your application never touches.
- Introduced vulnerabilities
These are added in your own Dockerfile layers: programming language runtimes, frameworks, libraries, build tools, and custom binaries. They are under the direct control of your development and platform teams and are more closely tied to your application’s design decisions.
For most organizations, inherited issues dominate the scanner output. Teams end up accountable for vulnerabilities that arrive “for free” with bloated base images, not because they wrote risky code. CleanStart Images collapse this inherited attack surface so security teams start from a much cleaner baseline and can focus on issues introduced by their own code.
Base images and dependency amplification
Base images act as dependency amplifiers: every extra package they contain is a new opportunity for CVEs. The academic study cited earlier demonstrated a strong linear relationship between package count and vulnerability count, measuring around 1.7 vulnerabilities per package on average before updates.
This means that:
- A bloated base with 300 packages can easily carry 500+ vulnerabilities by default.
- Adding just 50 unnecessary packages may bring in 80–100 more CVEs, multiplied across every workload that inherits that base.
As organizations standardize on a small set of base images, a single vulnerable version of a library such as OpenSSL or glibc can appear in every microservice, every cluster, and every environment. Thus, dashboards display thousands of common threats, even if the application's code is relatively small and well-maintained.
CleanStart Images invert this pattern by shipping only the essential components needed by each workload, dramatically reducing both package and vulnerability counts.
The endless patch and rebuild cycle
Container best practice says you should rebuild and redeploy images with updated components rather than patching running containers. While this is architecturally sound, it creates a patch–rebuild–redeploy treadmill:
- New CVEs are discovered, and scanners produce fresh reports.
- Security teams triage issues, open tickets, and negotiate priorities with product teams.
- Developers bump versions, update base image tags, run CI pipelines, and wait for tests.
- New images get deployed through staging and production, often with change management overhead.
Industry analysis shows that investigating and planning remediation for a single vulnerability can consume hundreds of dollars of engineering time, especially in large organizations with strict processes. One application security ROI study estimated that teams spend 10,584 developer hours per year on remediation alone, at an average fully loaded rate of $71.50 per hour, totaling about $ 756,000 in annual remediation costs per organization. Yet in real-world environments, 71% of highseverity vulnerabilities with available fixes remain unpatched, and only about 15% of critical and high CVEs are in runtimeloaded packages, meaning significant effort is spent on issues that may never be exploitable.
Why updating base images rarely fixes the problem
“Just update the base image” is a common recommendation, but data suggests it only partially addresses the problem. In the container vulnerability study, updating packages did cut vulnerabilities from about 1.7 to 0.6 per package, but overall images remained heavily vulnerable because they still shipped many unnecessary packages. A hardened image report that compared baseline, debloated, and hardened images found:
- Debloated images (same base family, fewer packages) reduced total CVEs by about 64% on average.
- Hardened images (minimal, securityfocused) achieved about 99% fewer CVEs on average, often shipping with zero known CVEs at build time compared to hundreds in the baseline.
- Some “secure” curated images still carried around 110 CVEs on average, including multiple high and critical issues, while hardened equivalents had zero known CVEs.
The takeaway is that patching inside a bloated image has diminishing returns; the real leverage comes from radically shrinking what is inside the image in the first place. Cleanstart hardened images embody this approach by starting minimal, enforcing strict supplychain controls, and continuously maintaining nearzero CVEs, which is far easier to manage at a global scale.
The real cost of repeated vulnerability remediation
CVE fatigue is an economic problem as much as a technical one. When you have hundreds of vulnerabilities per image and thousands across your environment, each ticket incurs:
Time for triage, risk assessment, and coordination between security, DevOps, and product teams.
- Time for implementation, testing, and deployment, often with changemanagement governance in regulated industries such as BFSI, healthcare, and telecom.
Across large fleets, this can translate into millions of dollars per year spent just to keep up with vulnerability reports, especially when many of those CVEs are in unused components or nonruntime code paths. In this context, shifting to hardened, minimal images that remove 60–99% of CVEs by design is not just a security improvement; it is a significant costoptimization strategy.
CleanStart's software composition analysis integrates seamlessly to reduce SCA noise and cut costs by 25–40% through fewer incidents and remediation.
Breaking the CVE fatigue cycle with reduced attack surface
To break the CVE fatigue cycle, the goal should be fewer meaningful CVEs, not “zero CVEs everywhere.” That requires a shift in design principles:
- Use minimal, purposebuilt base images
Start from images that contain only the OS components and libraries your workload needs. This alone can cut vulnerability counts dramatically because you remove entire classes of unused software from your images.
- Debloat and harden images
Remove build tools, shells, debuggers, and unused runtimes from production images using multistage builds and strict Dockerfile hygiene. Hardened images based on this approach have shown up to 99% fewer CVEs compared to common community images.
- Prioritize runtimereachable vulnerabilities
Focus remediation on vulnerabilities in packages that are actually loaded and reachable in production, which account for roughly 15% of critical and high CVEs in typical environments. This aligns effort with real exploitability instead of headline CVE counts.
Platforms and solutions that provide curated, hardened, and continuously updated images (similar to what Cleanstart advocates) give teams a practical way to operationalize this strategy without building it all inhouse. By combining minimal images, strong supplychain controls, and runtimeaware prioritization, organizations can reduce CVE fatigue, improve security posture, and streamline compliance reporting across regions.
Fixing fewer CVEs by design
CVE fatigue arises because traditional approaches treat every vulnerability as equal, stuff too much software into each container, and push patching responsibilities onto already overloaded teams. The data shows that containers commonly ship with 300–600+ vulnerabilities per image, 87% of images have critical or high issues, and the majority of those vulnerabilities are not in runtimereachable code.
By shifting to lean, hardened, minimal images and focusing on runtimereachable CVEs, organizations can cut vulnerability counts by 60–99%, reduce remediation workload, and get much closer to realistic, riskbased security. For teams working in diverse geographies and regulatory landscapes, this designfirst approach scales far better than endless patch sprints and gives stakeholders a clearer story: you are not just fixing more CVEs, you are designing systems that ship with fewer CVEs in the first place.
FAQ
What is CVE fatigue in container security?
CVE fatigue is the burnout and loss of effectiveness that happens when teams face constant vulnerability alerts, large backlogs, and ongoing pressure to “fix everything” despite limited resources. It is especially common in container environments where most images ship with hundreds of CVEs, and 87% of production images contain critical or highseverity issues.
Why do my container images always show so many vulnerabilities?
Most images are built from generalpurpose base OS distributions and include many unused packages, each of which may carry multiple CVEs. Studies show an average of 460–600+ vulnerabilities per container and about 1.7 vulnerabilities per package, so even small increases in package count significantly inflate scanner results.
Does updating base images remove all container CVEs?
No. Updating base images and packages is necessary but not sufficient, because bloated images still bring in unused components and “will not fix” vulnerabilities. Hardening and debloating images has been shown to reduce CVEs by around 64%, while hardened minimal images can reach about 99% fewer CVEs than standard baselines.
What is the most effective way to reduce container CVEs longterm?
The most effective approach is to reduce the attack surface by design using minimal, hardened base images and strict dependency control, then prioritize vulnerabilities that are actually reachable at runtime. This strategy shrinks the backlog across clusters and regions, lowers remediation cost, and works well for global organizations operating under varying regulatory regimes.
How does a hardenedimage strategy (like Cleanstart’s) help with GEO and compliance requirements?
Hardened images that start near zero known CVEs, with transparent SBOMs and continuous updates, make it easier to demonstrate due diligence to regulators and auditors in diverse jurisdictions such as India, the EU, and the US. CleanStart's Software Bill of Materials (SBOM) provides the transparency needed for FIPS 140-3, SLSA Level 4, RBI, and DORA compliance from the start.

.svg)
.webp)
.png)




.png)



.webp)
.webp)
.webp)







%20(1).png)



